Token Based Software
Secured authentication to databases and systems is essential to enterprise cybersecurity management. According to the 2023 Data Breach Investigations Report, 82% of all breaches stem from human error, often due to mishandled or compromised login details that allow malicious entities unauthorized access to network resources.
Fortunately, there’s an approach that guarantees security without the vulnerabilities inherent in conventional, credential-based methods: token-based authentication.
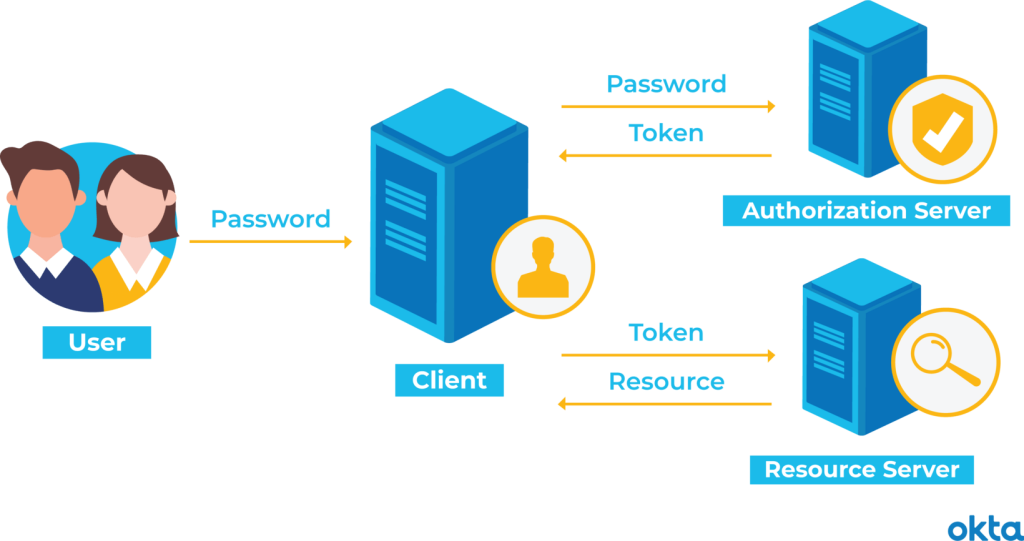
Token-based authentication is a security protocol that uses a unique, encrypted token to validate users rather than standard credentials such as username and password. Following successful initial authentication, the system generates a token, which is typically made up of encoded data about the user’s identity and session details.
This token is sent to the user and subsequently required for accessing protected resources, ensuring that users don’t have to provide their credentials over and over again. The token often is short-lived and can be used for Single Sign-On (SSO) across different services, reducing potential points of compromise and enhancing the user experience.